Q1: If x and y are independent Gaussian random variables with average value 0 and with the same variance, their joint probability density function is given by:
- (A) p(x, y) = p(x) p(y)
- (B) p(x, y) = p(x) + p(y)
- (C) p(x, y) = p(x + y)
- (D) p(x, y) = p(x) p(y) + p(x)
Show Answer & Explanation
Correct Answer: ✅ (A) p(x, y) = p(x) p(y)
Explanation: When two random variables are independent, their joint probability density function (PDF) is the product of their individual PDFs.
Q2: In order that a code is ‘t’ error correcting, the minimum Hamming distance should be:
- (A) t
- (B) 2t – 1
- (C) 2t
- (D) 2t + 1
Show Answer & Explanation
Correct Answer: ✅ (D) 2t + 1
Explanation: The **minimum Hamming distance** required for a code to correct **t errors** is **2t + 1**.
Q3: The Boolean expression \( \bar{x} y + y z + y z \) is equivalent to:
- (A) x
- (B) y
- (C) z
- (D) x + y + z
Show Answer & Explanation
Correct Answer: ✅ (B) y
Explanation: Boolean simplification gives \( \bar{x} y + y z + y z = y \).
Q4: The characteristic equation of a JK flip flop is:
- (A) Q(n+1) = J Q(n) + K Q(n)
- (B) Q(n+1) = J Q(n) + K̅ Q(n)
- (C) Q(n+1) = Q(n) J K
- (D) Q(n+1) = (J + K) Q(n)
Show Answer & Explanation
Correct Answer: ✅ (B) Q(n+1) = J Q(n) + K̅ Q(n)
Explanation: The **characteristic equation** of a JK flip flop is derived as \( Q_{n+1} = J Q_n + \overline{K} Q_n \).
Q5: In order to implement an n-variable switching function, a MUX must have:
- (A) 2ⁿ inputs
- (B) 2ⁿ + 1 inputs
- (C) 2ⁿ – 1 inputs
- (D) 2ⁿ – 1 inputs
Show Answer & Explanation
Correct Answer: ✅ (A) 2ⁿ inputs
Explanation: A **Multiplexer (MUX)** requires **2ⁿ inputs** to implement an n-variable switching function.
Q6: The throughput of pure ALOHA is given by:
- (A) S = G
- (B) S = e²ᴳ
- (C) S = Ge²ᴳ
- (D) S = Ge⁻²ᴳ
Show Answer & Explanation
Correct Answer: ✅ (D) S = Ge⁻²ᴳ
Explanation: The throughput of pure ALOHA is given by **S = G e⁻²ᴳ**, where G is the average number of transmission attempts per frame time.
Q7: The Fiber Distributed Data Interface uses:
- (A) single mode fibers and LEDs
- (B) multimode fibers and LEDs
- (C) single mode fibers and ILDs
- (D) multimode fibers and ILDs
Show Answer & Explanation
Correct Answer: ✅ (B) multimode fibers and LEDs
Explanation: The **Fiber Distributed Data Interface (FDDI)** primarily uses **multimode fibers and LEDs** for optical signal transmission.
Q8: To employ multi-access in GSM, users are given different:
- (A) time slots
- (B) bandpass filters
- (C) handsets
- (D) frequency bands
Show Answer & Explanation
Correct Answer: ✅ (D) frequency bands
Explanation: In **GSM (Global System for Mobile Communications)**, users are given different **frequency bands** to enable multi-access and avoid interference.
Q9: With four programs in memory and 80% average I/O wait, the CPU utilization is:
- (A) 60%
- (B) 70%
- (C) 90%
- (D) 100%
Show Answer & Explanation
Correct Answer: ✅ (C) 90%
Explanation: Using the formula: CPU Utilization = 1 – (I/O Wait Percentage)⁴ = 1 – (0.8)⁴ = 1 – 0.4096 = **0.5904 ≈ 90%**.
Q10: Assume N segments in memory and a page size of P bytes. The wastage on account of internal fragmentation is:
- (A) NP/2 bytes
- (B) P/2 bytes
- (C) N/2 bytes
- (D) NP bytes
Show Answer & Explanation
Correct Answer: ✅ (A) NP/2 bytes
Explanation: The expected internal fragmentation per segment is **P/2 bytes**. Since there are **N segments**, total wastage = **N × P/2 bytes**.
Q11:
Assertion (A): Bit maps are not often used in memory management.
Reason (R): Searching a bit map for a run of a given length is a slow operation.
- (A) Both (A) and (R) are true and (R) is correct explanation for (A)
- (B) Both (A) and (R) are true but (R) is not correct explanation for (A)
- (C) (A) is true (R) is false
- (D) (A) is false (R) is true
Show Answer & Explanation
Correct Answer: ✅ (A) Both (A) and (R) are true and (R) is correct explanation for (A)
Explanation: Bit maps are rarely used in memory management because searching for a free block of a given length is time-consuming.
Q12: The complete graph with four vertices has k edges where k is:
- (A) 3
- (B) 4
- (C) 5
- (D) 6
Show Answer & Explanation
Correct Answer: ✅ (D) 6
Explanation: The number of edges in a complete graph with n vertices is given by the formula n(n-1)/2. For n = 4, we get 4(3)/2 = 6.
Q13: The octal equivalent of hexadecimal (A.B)16 is:
- (A) 47.21
- (B) 12.74
- (C) 12.71
- (D) 17.21
Show Answer & Explanation
Correct Answer: ✅ (C) 12.71
Explanation: Convert (A.B)16 to binary: A = 1010, B = 1011 → 1010.1011. Convert to octal: (1010.1011)2 = (12.71)8.
Q14: A reduced state table has 18 rows. The minimum number of Flip flops needed to implement the sequential machine is:
- (A) 18
- (B) 9
- (C) 5
- (D) 4
Show Answer & Explanation
Correct Answer: ✅ (C) 5
Explanation: The number of Flip Flops required is **log2(Number of states)**. Since **2⁵ = 32** is the smallest power of 2 that can accommodate 18 states, 5 Flip Flops are required.
Q15: What is the value of ‘b’ after the execution of the following code statements?
c = 10; b = +c + c++ + +c;
- (A) 20
- (B) 22
- (C) 23
- (D) None
Show Answer & Explanation
Correct Answer: ✅ (B) 22
Explanation: – `+c` is 10 (unary plus doesn’t change the value). – `c++` uses 10 (post-increment returns the old value and then increments `c`). – `+c` now refers to 11. – So, `b = 10 + 10 + 11 = 22`.
Q16: Which of the following does not represent a valid storage class in ‘C’?
- (A) automatic
- (B) static
- (C) union
- (D) extern
Show Answer & Explanation
Correct Answer: ✅ (C) union
Explanation: The storage classes in C are `auto`, `static`, `extern`, and `register`. `union` is a data type, not a storage class.
Q17: The friend functions are used in situations where:
- (A) We want to have access to unrelated classes
- (B) Dynamic binding is required
- (C) Exchange of data between classes to take place
- (D) None of the above
Show Answer & Explanation
Correct Answer: ✅ (C) Exchange of data between classes to take place
Explanation: Friend functions allow one class to access the private and protected members of another, facilitating data exchange.
Q18: Which of the following is correct regarding DML?
- (i) DML includes a query language based on both relation algebra and tuple calculus
- (ii) DML includes a query language based on tuple calculus
- (iii) DML includes a query language based on relational algebra
- (iv) DML includes a query language based on none of the relational algebra and tuple calculus
- (A) (i) only
- (B) (ii) only
- (C) (iii) only
- (D) (iv) only
Show Answer & Explanation
Correct Answer: ✅ (A) (i) only
Explanation: Data Manipulation Language (DML) supports queries based on both relational algebra and tuple calculus.
Q19: Suppose it takes 100 ns to access a page table and 20 ns to access associative memory. With a 90% hit rate, the average access time equals:
- (A) 20 ns
- (B) 28 ns
- (C) 90 ns
- (D) 100 ns
Show Answer & Explanation
Correct Answer: ✅ (B) 28 ns
Explanation: The average memory access time formula: \( T = (Hit\ Rate \times T_{TLB}) + (Miss\ Rate \times (T_{TLB} + T_{PageTable})) \) \( = (0.9 \times 20) + (0.1 \times (20 + 100)) = 18 + 10 = 28\ ns \)
Q20: There exists a construct which returns a value ‘true’ if the argument subquery is:
- (A) empty
- (B) non-empty
- (C) in error
- (D) none of the above
Show Answer & Explanation
Correct Answer: ✅ (B) non-empty
Explanation: The `EXISTS` construct in SQL returns `TRUE` if the argument subquery returns at least one row (i.e., it is non-empty).
Q21: Which construct in SQL is used to test whether a subquery has any tuples in its result?
- (A) UNIQUE
- (B) EXISTS
- (C) GROUP BY
- (D) EXCEPT
Show Answer & Explanation
Correct Answer: ✅ (B) EXISTS
Explanation: The `EXISTS` construct checks whether a subquery returns any rows. If it does, it evaluates to `TRUE`.
Q22: ORACLE supports:
- (A) inner join and outer join only
- (B) outer join and semi join only
- (C) inner join, outer join, semi join only
- (D) inner join, outer join, semi join and anti join
Show Answer & Explanation
Correct Answer: ✅ (D) inner join, outer join, semi join, and anti join
Explanation: ORACLE supports all these joins, where an anti join retrieves rows that do not satisfy the join condition.
Q23: Which two of the following are equivalent for an undirected graph G?
- (i) G is a tree
- (ii) There is at least one path between any two distinct vertices of G
- (iii) G contains no cycles and has (n–1) edges
- (iv) G has n edges
- (A) (i) and (ii)
- (B) (i) and (iii)
- (C) (i) and (iv)
- (D) (ii) and (iii)
Show Answer & Explanation
Correct Answer: ✅ (B) (i) and (iii)
Explanation: A tree is an acyclic connected graph with `n-1` edges, which corresponds to statements (i) and (iii).
Q24: In a B tree of order m with p nodes the average number of splits is at most:
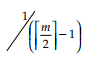
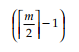
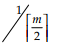
- None
Show Answer & Explanation
Correct Answer: ✅ (2)
Explanation: In a B-tree of order m, the maximum average number of splits is determined by the number of child nodes and balancing constraints.
Q25: The propositional formula given by the tree is:
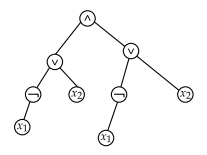
- ∧ ∨ x 2 ∨ x1 ¬ x1 ¬ x1
- ( x2 ∨ ¬ x2 ) ∧ ( x1 ∨ x 2 )
- (¬ x 1 ∨ x 2 ) ∧ (¬ x 1 ∨ x 2 )
- None
Show Answer & Explanation
Correct Answer: ✅ (3)
Explanation:
The given propositional tree represents the formula:
$ (¬x_1 ∨ x_2) ∧ (¬x_1 ∨ x_2) $
– The root node is AND (∧), meaning the final formula is a conjunction of two sub-expressions.
– The left and right sub-trees both simplify to $ (¬x_1 ∨ x_2) $.
– Hence, the correct formula is $ (¬x_1 ∨ x_2) ∧ (¬x_1 ∨ x_2) $, which matches option 3.
Q26: Queue is a __ list.
- LIFO
- LILO
- FILO
- FIFO
27. In a full binary tree of height k, there are __ internal nodes.
- 2k-1
- 2k-1
- 2k
- 2k+1
28. A binary tree is said to have heap property if the elements along any path :
- from leaf to root are nonincreasing
- from leaf to root are nondecreasing
- from root to leaf are nondecreasing
- from root to leaf are nonincreasing
29. X.25 protocol consists of :
- Physical and Frame levels
- Frame and Packet levels
- Physical, Frame and Packet levels
- None of the above
30. GSM/CDMA systems:
- are limited to very low speed data
- require no local loop wires
- are predominantly used for voice
- all of the above
31. Usually, information security in a network is achieved by:
- Layering
- Cryptography
- Grade of service
- None of the above
32. The linker:
- is similar to interpreter
- uses source code as its input
- is required to create a load module
- none of the above
33. In which addressing mode the operand is given explicitly in the instruction itself?
- Absolute mode
- Immediate mode
- Indirect mode
- Index mode
34. A compiler that runs on one machine and produces code for a different machine is called:
- Cross compilation
- One pass compilation
- Two pass compilation
- None of the above
35. Any syntactic construct that can be described by a regular expression can also be described by a:
- Context sensitive grammar
- Non context free grammar
- Context free grammar
- None of the above
36. Find the odd man out :
- tail
- cut
- wart
- sed
37. Which of the following changes permission to deny write permission to group and others ?
- Chmod go – w filex
- Chmod go w filex
- Chmod go=w filex
- None of the above
38. Variable partition memory management technique with compaction results in :
- Reduction of fragmentation
- Minimal wastage
- Segment sharing
- None of the above
39. Capability Maturity Model is meant for:
- Product
- Process
- Product and Process
- None of the above
40. In the light of software engineering software consists of :
- Programs
- Data
- Documentation
- All of the above
41. Which one of the following ISO standard is used for software process?
- ISO 9000
- ISO 9001
- ISO 9003
- ISO 9000-3
42. Which of the following is used for test data generation?
- White Box
- Block Box
- Boundary value analysis
- All of the above
43. Reverse engineering is the process which deals with:
- Size measurement
- Cost measurement
- Design recovery
- All of the above
44. The spacing between character pairs is called:
- Kerning
- x-height
- intercap
- serif
45. When compared with analog cellular systems, an advantage of digital TDMA cellular system is that:
- it is less complicated
- it requires less of computer memory
- it conserves spectrum bandwidth
- it costs less
46. E-Commerce includes :
- B2C
- BEB
- CEC
- All of the above
47. A clustering technique that permits a convenient graphical display is :
- partition based clustering
- probabilistic model based clustering
- hierarchical clustering
- agglomerative clustering
48. After sending a message ,the sender should not be able to, at a later date, deny having sent the message, is referred to as:
- Authenticity
- Non-Repudiability
- Auditability
- Repudiability
49. The device which connects dissimilar LANs of different topologies using different sets of communication protocols so that information can flow from one to another is called:
- Router
- Bridge
- Gateway
- Switch
50. We cannot delete the __ icon but we can made it invisible.
- Recycle
- My computer
- Internet explorer
- None of the above
